Data Destruction Process: Best Practices
Data protection is the most critical issue when planning your IT decommissioning process. Therefore, we have designed information destruction solutions to comply with best practices detailed by NAID, NIST 800-88, and HIPAA auditors.
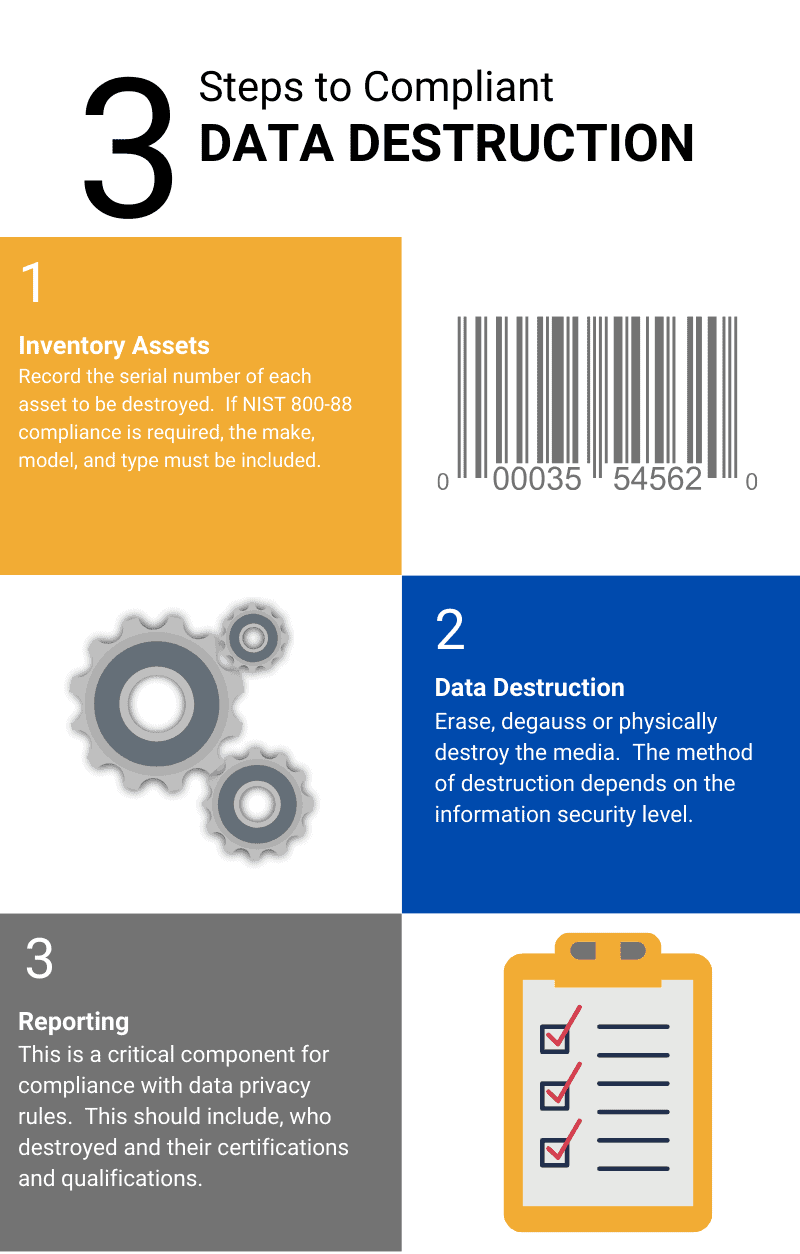
The simple three-step process to securely destroy digital media and pass compliance audits.
We are performing an audit of the IT department’s records. For compliance with HIPAA, we need to confirm the data destruction process and Certificate of Destruction…

On-Site Data Destruction
Hard drives, SSDs, and backup tapes are moved from your data center to our shredding truck for processing. This practice allows you to witness and verify that drives have been recorded and destroyed.
Inventory Drives
Hard drives pulled from servers, storage arrays, and computers are staged in our scanning area. Once collected, drives are scanned and inventoried for a detailed Certificate of Destruction report.
NIST 800-88 requirements go beyond capturing the hard drive serial number. Compliance with NIST requires linking the hard drive to the associated computer. See details below in the Certificate of Destruction Report.


Physically Destroy Drives
Hard drives are then destroyed at 1,000 PC drives per hour. Physically destroying hard drives for data destruction satisfies NIST 800-88 and all other data privacy laws, such as HIPAA.
Certificate of Destruction
Our Certificate of Destruction details the quantity and type of digital destruction, serial number, location, and company personnel that witnessed the process.
NIST 800-88 Certificate of Destruction report requires, among other details, a link between the hard drive being destroyed and the computer from which it resided. This information includes the make and model of the hard drive and the source computer.
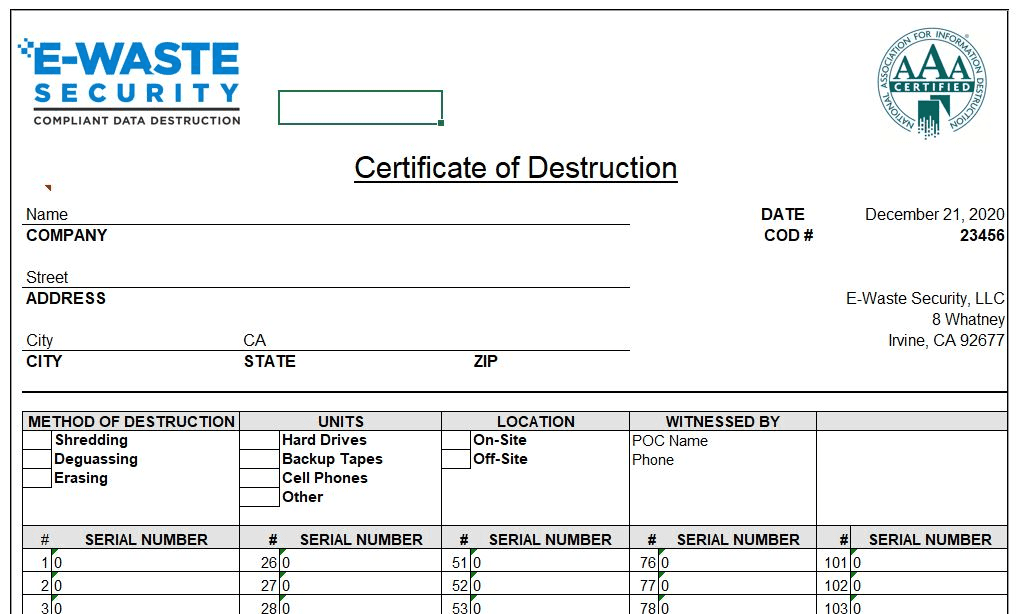
Our secure processes help organizations limit liability by complying with
